“I must trust that the benefit that I gain from using your service exceeds the concerns (Fear, Uncertainty, and Doubt) that I have about using it.”
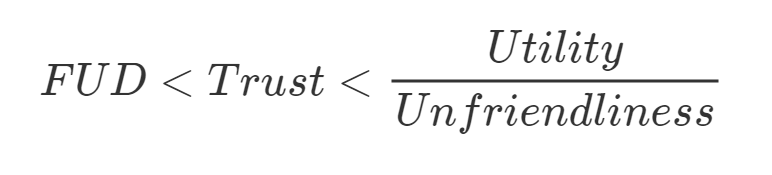
Benefit can be thought of as a ratio of utility to unfriendliness. No matter how user-friendly an application is, if a customer gains no utility from using the service, there is no incentive to use it. Conversely, waiting in line at the Division of Motor Vehicles is a great example of what is typically an “unfriendly” experience. However, the utility of a driver’s license is enormous and worth the inconvenience.
Now, let’s consider the other side of the equation—Fear, Uncertainty, and Doubt. Imagine a patient is contemplating brain surgery. It is natural for the patient to have all kinds of fear and uncertainty about the operation. In fact, she would forgo the procedure if she had serious doubts about the brain surgeon’s competency or her likelihood of a positive outcome for the surgery. Years ago, my grandma was in this very same situation. In her mid-80’s, she had a brain surgery to remove a tumor. She agreed to have the surgery after family members (which included my brother, a physician) looked into the risks and complications of the surgery and met with the surgeon. Unfortunately, the surgery did not eliminate the cancer, and she decided not to have a second surgery. She soon passed away.
I have purposefully used two examples that did not specifically involve computer systems in an attempt to make the Trust-Value Equation universally applicable. Now, let’s shift the discussion to cloud services. In the typical sales process, the decision makers at the customer organization are attracted by the benefits provided by the application and impressed with the usability of the application. Naturally, the next question is, “can I trust this application and the organization with our data?”
Savvy customers will have a systematic security review process that delves into the specific security controls that the service organization uses to protect customer data. Sophisticated and demanding customers are quite likely going to find some gaps and weaknesses in the security posture of the service provider. This is to be expected because these organizations are rapidly evolving to meet marketplace opportunities and security investments involve decisions about tradeoffs that the customer may not fully appreciate.
In other words, it boils down to this question:
“Do I trust that is the application secure enough for me for me to use for my commercial advantage?”
I believe that this is an ongoing calculation where customers continuously ask themselves whether the trust-value equation assumptions have changed. Service providers must focus on tilting the equation ever more in their favor by:
- Increasing the utility of the service,
- Improving the user-friendliness of the service, and
- Enhancing the perceived trustworthiness of the service.
Naturally, the best way to enhance the perceived trustworthiness of the application is to improve its security such that it will withstand scrutiny from each customer’s security experts. It is also important to articulate the security considerations of the service in a credible way without overstating it.
As you create and consume various services, consider this trust-value equation and how you can make it work in your favor.
